The information you give helps fight scammers. If you got a phishing email, forward it to the Anti-Phishing Working Group at
[email protected]. (link sends email) . If you got a phishing text message, forward it to SPAM (7726). Report the phishing attempt to the FTC at ReportFraud.ftc.gov. Saved searches Use saved searches to filter your results more quickly
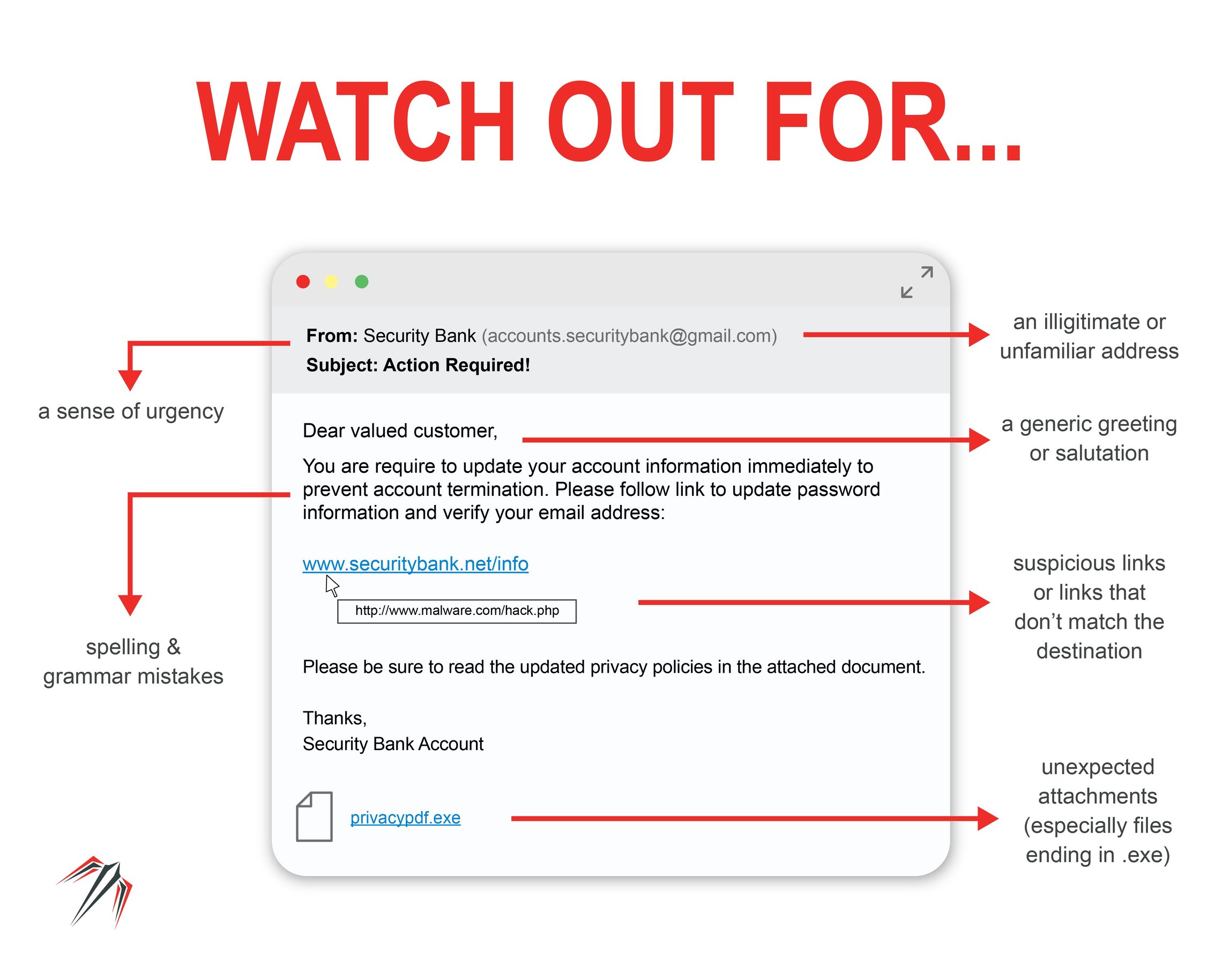
Don’t Get Hooked! 7 Signs of a Phishing Email
Protect yourself from phishing. Phishing (pronounced: fishing) is an attack that attempts to steal your money, or your identity, by getting you to reveal personal information -- such as credit card numbers, bank information, or passwords -- on websites that pretend to be legitimate. Cybercriminals typically pretend to be reputable companies. 4. Legit companies know how to spell. Possibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact - there's actually a purpose behind bad syntax. Hackers generally aren't stupid. Types Email phishing. Phishing attacks, often delivered via email spam, attempt to trick individuals into giving away sensitive information or login credentials.Most attacks are "bulk attacks" that are not targeted and are instead sent in bulk to a wide audience. The goal of the attacker can vary, with common targets including financial institutions, email and cloud productivity providers, and. Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. The information is then used to access important.

Phishing Email Examples To Help You Identify Phishing Images
Phishing Scams and How to Spot Them. Phishing is a type of online scam that targets consumers by sending them an e-mail that appears to be from a well-known source - an internet service provider, a bank, or a mortgage company, for example. It asks the consumer to provide personal identifying information. Then a scammer uses the information to. Avoid phishing messages & content. To help you avoid deceptive messages and requests, follow these tips. 1. Pay attention to warnings from Google. Google uses advanced security to warn you about dangerous messages, unsafe content, or deceptive websites. If you receive a warning, avoid clicking links, downloading attachments, or entering. Phishing email example: Instagram two-factor authentication scam. Two-factor authentication, or 2FA, is one of the best ways to protect your personal or financial information. When you log onto a site — say your online bank or credit card provider — you'll have to provide your username and password as usual. A phishing email is an email that appears legitimate but is actually an attempt to get your personal information or steal your money. Here are some ways to deal with phishing and spoofing scams in Outlook.com. Spoof Intelligence from Microsoft 365 Advanced Threat Protection and Exchange Online Protection help prevent phishing messages from.

Hoe kun je nepmails en phishing herkennen? Antagonist
Email phishing. The most common form of phishing, this type of attack uses tactics like phony hyperlinks to lure email recipients into sharing their personal information. Attackers often masquerade as a large account provider like Microsoft or Google, or even a coworker. Malware phishing. Another prevalent phishing approach, this type of attack. In recent years, advancements in Internet and cloud technologies have led to a significant increase in electronic trading in which consumers make online purchases and transactions. This growth leads to unauthorized access to users' sensitive information and damages the resources of an enterprise. Phishing is one of the familiar attacks that trick users to access malicious content and gain.
Phishing puts individuals, companies, educational institutions and others at risk due to the possibility of allowing the bad guys to gain access to financial information, personal data, proprietary company information, health information, student data and much more. Phishing is a cyberthreat hackers use to trick individuals into revealing sensitive information, such as passwords and personally identifiable information. In this guide, we'll shed light on how phishing works, how you can spot an attack, and how security software like Norton 360 Deluxe can help defend against phishing attacks by protecting.
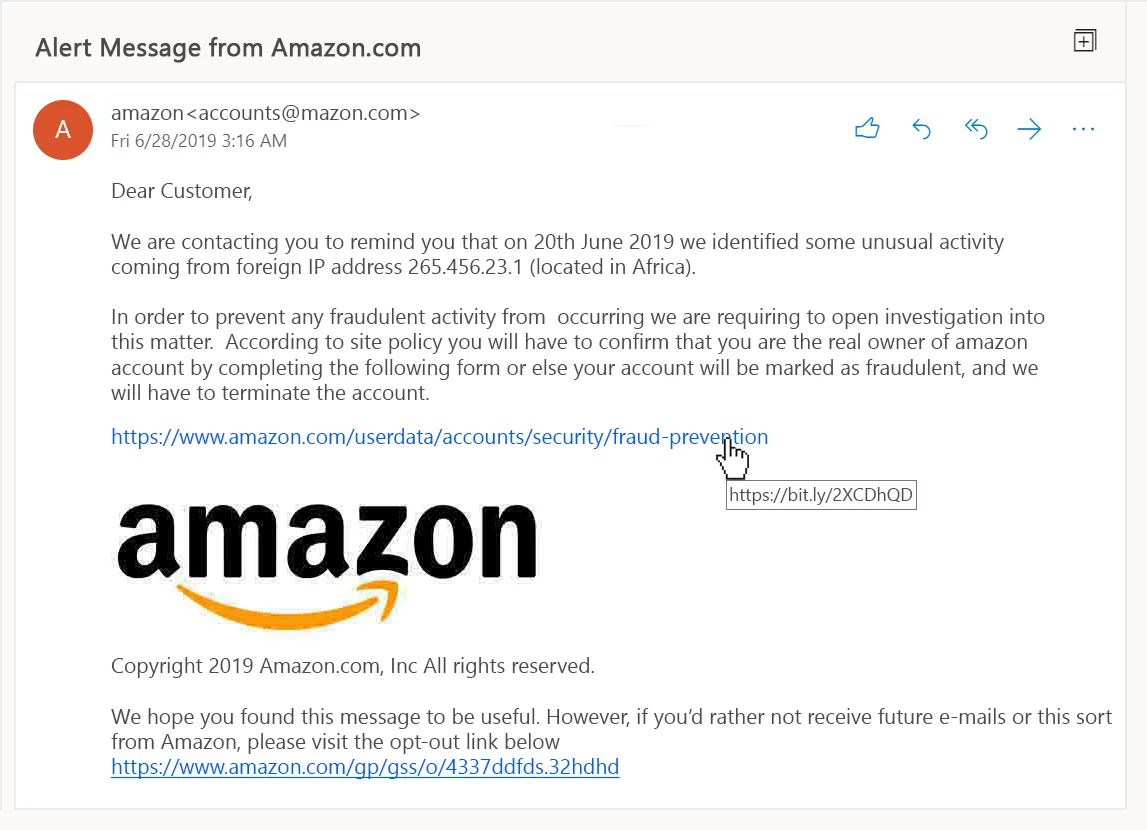
How to Spot Phishing Emails and Other Online Scams • Optima Systems
HTTPS phishing prevention tip: Always look closely at the URL of a site before logging in. 3. Email phishing. One of the most common phishing attacks is email phishing. Email phishing is when a cyberattacker sends you an email pretending to be someone else in hopes that you'll reply with the information they requested. Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim's machine. Phishing is a common type of cyber attack that everyone should learn.




