# camera-hacking Star Here are 18 public repositories matching this topic. Language: All Sort: Most stars techchipnet / CamPhish Star 2.6k Code Issues Pull requests Grab cam shots from target's phone front camera or PC webcam just sending a link. hack hacking penetration-testing termux kali-linux android-hacking camera-hacking techchip Another video with Master Hacker OccupyTheWeb! This time on Hacking IP Cameras in a video that will demonstrate how to gather info publicly on assets, tools.

All The Secrets Of Hacking Is Exposed Hack The IP Based CCTV Cameras
Cameradar allows you to Detect open RTSP hosts on any accessible target host Detect which device model is streaming Launch automated dictionary attacks to get their stream route (e.g.: /live.sdp) Launch automated dictionary attacks to get the username and password of the cameras Retrieve a complete and user-friendly report of the results CamSploit v1.0.1. CamSploit is an exploiting tool that helps in the IP camera pentest. It was developed using Dot Net Core (compatible with Windows and Linux), tested in windows 10 and Ubuntu 16. It has got a modular collection of exploits. You can create your own modules to expands the currents exploits. CamSploit is distributed under the GNU. In 2021, a Swiss white-hat hacker named Tillie Kottmann hacked into 150,000 commercial Verkada security cameras, including cameras in hospitals, schools, police departments, and prisons.1 lives. Unfortunately, IoT devices (like IP cameras, smart TVs, etc.) present a huge attack surface for cybercriminals to easily gain access to your network as they are highly vulnerable and easy to hack into. The security risk is real as 67% of enterprises and 82% of healthcare organizations have experienced IoT security incidents. IoT device are.
ip camera hacking YouTube
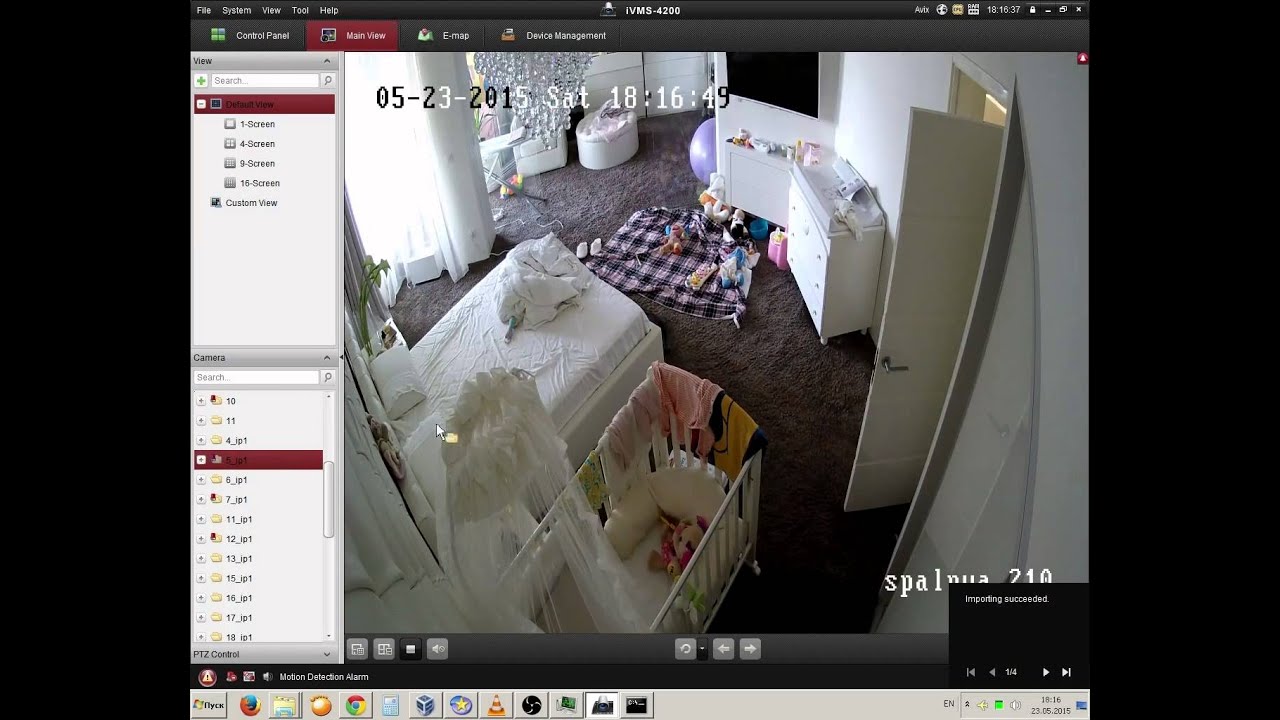
The interactive map below shows a sample of hacked and vulnerable Hikvision IP cameras across the USA and Europe. Hover over a marker to see an image from that camera: [Note: this report and map was originally published on Dec 18th for the USA only. We have now updated it to include / display European cameras.] Thousands of wireless IP cameras are vulnerable to remote attacks. At Hack in the Box security conference, researchers showed how to exploit the devices in "To Watch or Be Watched: Turning. The exposed cameras it discovered online are all CCTV/ IP cameras that can be used for CCTV surveillance both outdoors and indoors. This means that they could be recording everything from a. There's one way to check this; they all found out the root password for the device as "123456". Now let's try it out. Note: This is now running on my wireless network to make it more convenient for me, hence the IP address change: [dave@jotunheim ~]$ telnet 192.168..23. Trying 192.168..23…. Connected to 192.168..23.
Ip Cam Raids IP Cam Trolling YouTube
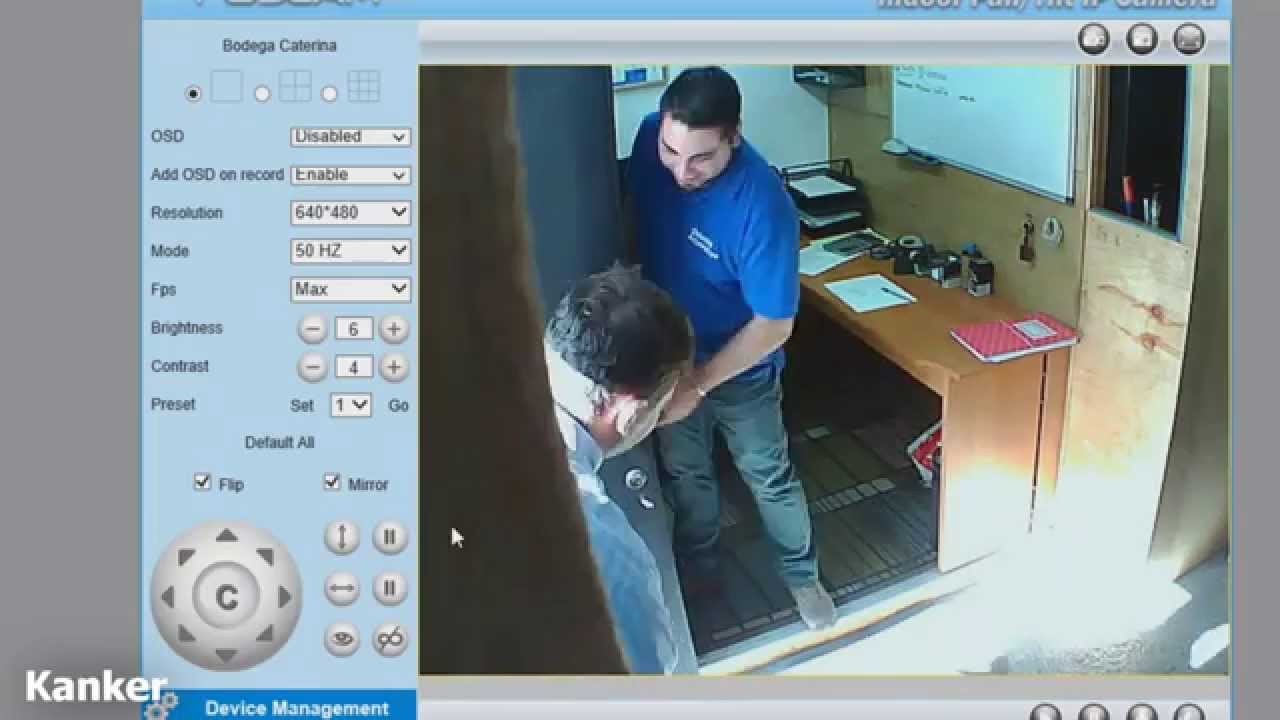
The flaw in the CCTV camera allows the "hackers" to watch everything the BBC employee types. Thankfully for the man being watched, the hacker is working with the BBC. This is part of a series of. Are your IP cameras safe? Too easy to hack?This is my third interview with the professional hacker Occupy The Web. In this video we dis.
IP cameras that store their video images onto SD cards inserted into the device are of particular concern. If the camera is hacked, the villain can readily access stored video and glean whatever information they can about the habits of the inhabitants. These security problems have initiated federal lawsuits against major manufacturers and. March 28, 2019. Security cameras used to be analog devices feeding back into a room full of tiny screens and commercial grade VCRs. As technology moved forward, IP cameras began to proliferate.
Supporting Zone How to Hack CCTV Private Cameras
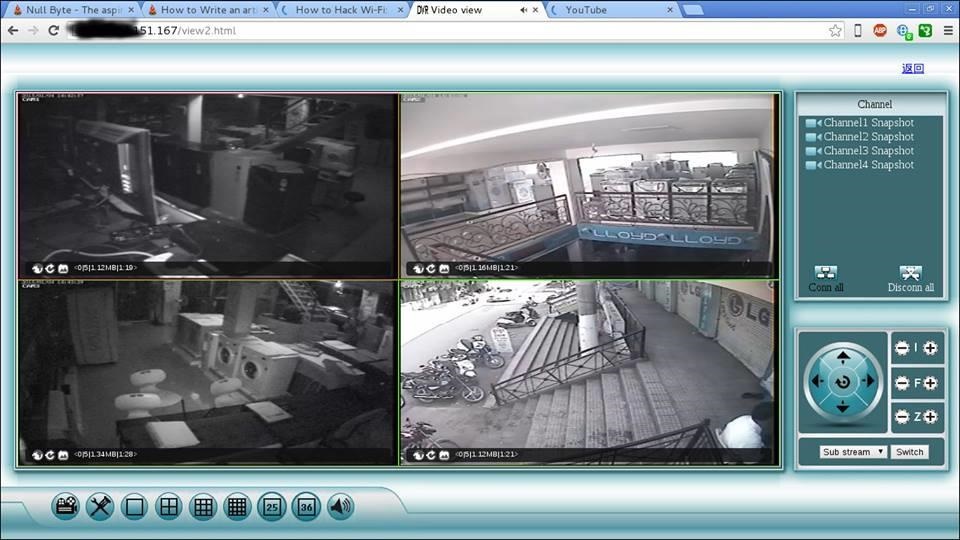
Search For "tag: IP Camera" on Criminal IP Gives a Total Result of 428,473 Exposed IP Camera Servers In some cases, hacked IP camera screens can be viewed without any login authentication. Hacked IP Camera Screen Exposed to the Internet Without Any Login Authentication IoT Quitely Becoming Infected Like a Zombie This can leave a number of IP cameras vulnerable to unauthorised viewing with the privacy of users at risk. Default unauthenticated access to camera feed. By default, the cameras feed can be accessed without a username and password.. This blog post is part one in a short series on learning some basic game hacking techniques. I've chosen.



